The internet is growing rapidly, and that means there is a need for several rules and systems that need to be put in place. These rules are the ones that allow you to transmit information from no matter the physical quantity or the kind of variation. Therefore, Spanning Tree Protocol or STP. In short, refers to rules that help in building loop-free signals when connected to computers. STP’s primary function is to ensure that there are no switch loops. Also, it helps in preventing radiation coming from the broadcast.
Table of Contents
The Spanning Tree Protocol has evolved over past years and also developed in a few different types.
The typical examples of the development of Spanning Tree Protocol include; standard STP or 802.1D, which is the original STP. There is the PVST, which is the improvement of the Cisco of Spanning Tree Protocol that adds a per VLAN feature. There is an RSTP, which is the latest version of the protocol, which is highly improved compared to the other types and has a much faster conversion. Also, there is a Rapid PVST, an improvement of RSTP that comes from Cisco that adds the feature of per VLAN.
Per VLAN Spanning Tree protocol is ideal for large networks with lots of switches and VLANs, as this feature helps you plan for an efficient network. The one thing that remains similar to all these different types of STP is that they use a similar method.
HOW LOOPS FORM
So, let’s define a standard Spanning Tree Protocol? A Standard Tree Protocol refers to a feature that stops loops by the use of less useful switches. Let’s take an instance, you have switches probably three in total, and you connect all of them, there is a high chance that a loop can easily form. When a loop creates between switches connected, there is a high chance you can run into some problems. A switch can react in a certain way when it gets a broadcast message from a specific address.
What that switch does is sends the message out to all other ports with the exception of the one that has it.
So, the switches that receive the broadcast message will too forward the message out, making a loop. These messages are always sent, and that means there are more and more frames that add to the loop. When these frames are so many, you can imagine how easy it is for the network to get clogged easily. The broadcast storm in Spanning Tree Protocol is the result of a large number of frames formed.
When the number continues to increase, the storm will continue getting bigger and bigger, which can result in one switch failing. The other kind of loop is where when a switch receives a message instead of it continuously sending the same message to other loops, and it will learn the message address. Therefore, if a switch gets similar messages often, it will now update the address tables when the broadcast storm keeps building up. The other loop problem you can experience is with duplicate problems.
The solution for such kinds of issues is that the device will have to prevent a port.
Therefore, the message will still get sent, and the port will receive the data, but it just ignores it and does not send the message. This way, we can easily prevent some of the significant problems that form from looping like the broadcast storm. When data cannot loop anymore, it means there is no broadcast storm, and the address is completely stabled and also that there are no frames made in duplicates.
HOW does SWITCH CHOOSE THE PORT TO BLOCK?
We have seen that we can easily find a solution to our looping problem, but the issue comes to how switches chose the port to block. The STP follows stringent rules that determine which kind of port that it has to prevent. I will highlight to you the overview of how the Spanning Tree Protocol chooses the port to block.
STEPS FOR USING A SPANNING TREE PROTOCOL
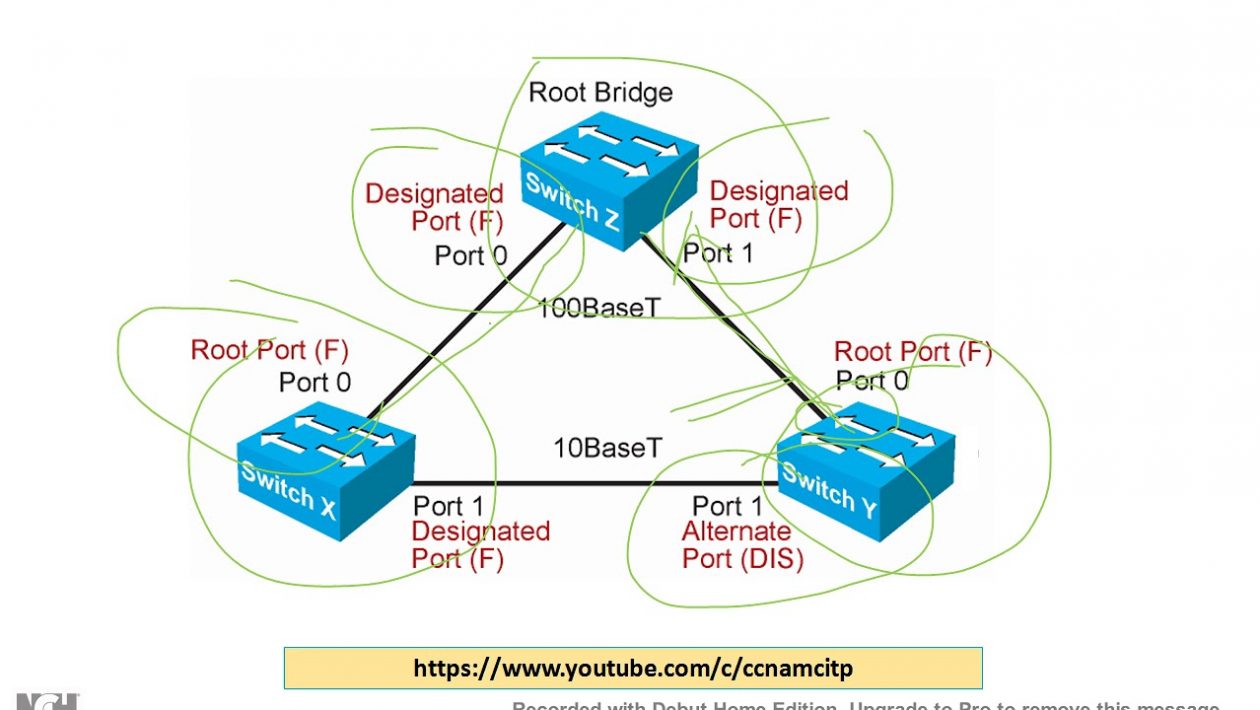
Step one is electing a root bridge. Selecting your root bridge means selecting the leader of all the devices. The second move is ensuring that the main bridge is the state of forward. The third thing is each of the switches that are not root will select the main port, and it has to be the good bridge.
The fourth thing is the devices that are left out will then choose to either be or not to be a port to be chosen. The final process is the remaining ports go in a state that they act like they are blocked, and this is the high overview of how the STPro works. Also, there is the PVST that adds the per VLAN feature, and it’s the Cisco default feature. However, we first need to know the port roles and states.
PORT ROLES AND STATES
ROLES
The port role in Spanning Tree Protocol means the job that it’s supposed to do. Root ports are the right ports you need to get to the main bridge. Some ports are designated, and they are ideal to use to the main bridge. The ports that are not designated fall to the state where they act blocked.
THE STATES
The states inform you of the type of state a port is in, and the state of a port changes if they shift to a different kind of job. An instance is where the assigned ports, together with the main ports being in a state of moving forward. A port can be disabled, and it means a port is off. This kind of port is the one that’s blocking traffic. When a block is in a listening state, it means that the block is not sending traffic and also not retaining addresses.
The other state that a port can be in Spanning Tree Protocol is the learning state. Here the port does not send any kind of traffic, and what it does is continuously learn the addresses. When in such a state of forward, a port can receive and send traffic normally. While in either the state of listening or a port learns, it also means it’s in a transitional space. When a port is at this space, it can change the function it does to another.
SPANNING TREE PROTOCOL PROCESS
We did state earlier that the thing you need to do initially is select the bridge that will act as a root. Therefore, switches will select the main bridge in a pretty straight-forward way. Each of the switches in a network has a PPDU, and the PPDU has a cost marked to the root, the price here refers to that of the main bridge, and the root, plus the BID.
The BID, or as most refer it the ID of the bridge,
is a crucial thing you need to take into consideration when selecting the main bridge. The part that’s in the first part has the STP that has a number of 32769, followed by the number of the VLAN. The other part contains the address. Therefore, the lowest overall BID provided in a switch makes it be the main bridge. All the switches can list themselves as the root and share the PPDU. However, the switches will not their strength is not enough, and the lower the BID in a device means that it will now become the main bridge.
After selecting the main is elected, all the ports will now enter a forwarding state.
Once they are in that state, they can then choose which path to take to the main bridge. These paths are the root of the port. The cost determines the ports’ root decision. To know the cost, you will add the outgoing port plus the root. The final step is blocking. All ports have to take a side, and if one is not the main bridge or a port that is designated, they end up in a state where they are blocked. This selection marks the final process of the STP selection overview.
TYPES OF LAN PROTOCOL
Apart from the Spanning Tree Protocol, there are other different types of LAN protocols available.
THE TCP OR THE INTERNET PROTOCOL, IP
This determines how you set and manage website conversations where you can exchange the data between the application’s programs. The Transmission Control Protocol together with the Internet Protocol, controls how you send data between the computers. Therefore, this protocol allows computers to communicate easily using the net.
THE FILE TRANSFER PROTOCOL FTP
In a network, you will need to transfer computer files from one computer5 to another. This can either be a server computer or the client computer, and therefore you will need a protocol. This File Transfer Protocol will allow you to transfer these files easily.
HYPERTEXT TRANSFER PROTOCOL or HTTP
This rule is responsible for transferring documents in a hypermedia format like the HTML. The protocol uses the client-server model hence giving you the ability to transmit stuff through the web.
ADVANTAGES OF STP
PREVENTS LOOPING
The big benefit you get from using the STP is preventing the loop from happening. Loops are a disaster in a network, and if you don’t prevent them, there is a high chance that the network can crash. This occurs when sending multiple data at the same time, and there is no right communication, thus causing clogging. Also, loops can result in data being sent to wrong places hence an issue. What the Spanning Tree Protocol does is it ensures that devices send the data and also communicate.
OFFERS BACKUP WHEN CONNECTION IS DOWN
The other advantage of using the Spanning Tree is it offers you back up when there are connection technicalities. One good thing about the STP is the numerous paths available to choose from. Therefore, when STP notices that there is one path that is not working correctly, it can close it immediately and open another one. This is an advantage as it ensures you are always connected to the internet.
MAKES THE BRIDGING LOGIC SIMPLE
The other advantage of the Spanning Tree is it helps in simplifying the logic of bridging. In computers, you can easily experience the problem of bridging between computers in the same network. The reason for this is because each of the devi9ce uses a different path to approach a similar system; therefore, it can cause a network failure. What the Spanning Tree Protocol does is to eliminate the confusion by making a root bridge that eliminates the problems that can occur.
DISADVANTAGES OF USING A SPANNING TREE PROTOCOL
IT FAILS BAD
One thing about the Spanning Tree Protocol is that it works well, but you can experience a significant problem if it fails. One thing you should know is that when STP fails, the whole domain collapses, and this can cause application problems. Therefore, many people perceive the Spanni9ng tree protocol as a very unreliable network protocol.
WASTES THE BANDWIDTH
In a Spanning Tree Protocol, there is a lot of network bandwidth that is either blocked or shut down. The blocking and shutting down of this network accumulate around 40% meaning more data is going to waste.
HUGE OPERATIONAL COST
There are enormous operational costs that you incur when operating with the Spanning Tree Protocol. The reason for this is because of several hacks, and they are trying to improve the protocol, thus requiring more cash.
CONCLUSION
To conclude, we have discussed a lot concerning the Spanning Tree Network, starting with the definition of the protocol. We have also seen how the protocol works and how you can easily set it up. We did talk about some of the advantages of the Spanning Tree Protocol and its disadvantages. Also, the article discusses the other types of LAN protocols that you can take advantage of and more content.
FAQ
What is the use of a Spanning Tree Protocol?
This network protocol that the ethernet networks commonly use to prevent a loop and also broadcast storms.
What is the function of an Ethernet switch?
The primary function of the ethernet switch is to provide a multiport layer two bridging functions, and some perform functions of another layer.
Is Spanning Tree Protocol still in use?
This network protocol is still in use even though people are trying to replace it with other networking protocols.